What is a DDoS attack?
Distributed denial-of-service (DDoS) attacks explained.
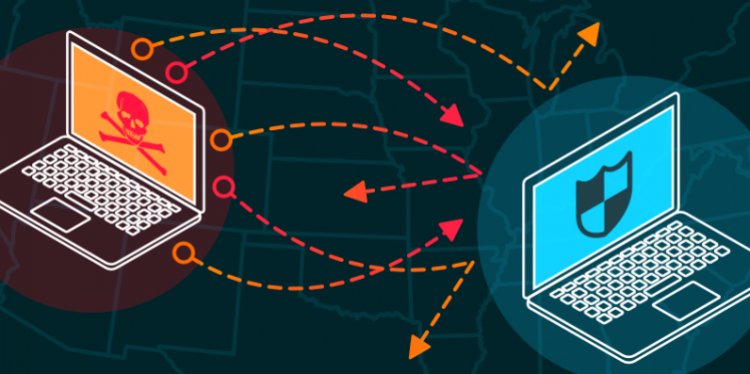
In a DDoS attack, a flood of Internet traffic is used to interrupt the usual traffic of a targeted server, service, or network.
An effective DDoS assault employs numerous compromised computer systems as attack traffic sources. Computers and other networked resources, including internet of things (IoT) devices, are all examples of exploited machinery.
A DDoS attack is, in a very broad sense, like unforeseen traffic congestion causing havoc on the highway, diverting traffic away from its normal route.
How does Distributed Denial of Service (DDoS) attacks work?
Distributed Denial of Service (DDoS) assaults are executed utilizing networks of Internet-connected machines. Because of malware, computers and other devices (such as IoT devices) have been infected and put under the control of an attacker, who uses them to his or her advantage. A set of devices known as "bots", "zombies" is referred to as a botnet.
The more computers within a botnet that have been built, the more remote instructions that can be sent to each bot, which helps to launch an assault. A victim's server or network can be overrun if each bot in the botnet makes queries to the target's IP address. Bots are genuine Internet devices, and it is, therefore, difficult to properly separate the attack traffic from the typical traffic.
How to recognize a distributed denial of service attack
A DDoS assault is noticeable because of a sudden slowdown or outage of a website or service. Additional analysis is frequently required because several reasons might produce identical performance concerns, such as real spikes in traffic. Inspecting your traffic logs for telltale symptoms of a DDoS assault can be accomplished with traffic analytics tools.
- Unexpected patterns of network traffic flow emanating from a single IP address or range of addresses are called suspicious
- Users sharing a single behavioral profile, such as the type of device, location, or browser version, flood the site with traffic
- An unexplained increase in the number of requests to a specific URL or endpoint
- Inconsistent traffic patterns that only appear strange at unusual times of the day (e.g. a spike every 10 minutes)
 Alexander
Alexander 








