Thousands of Citrix Servers Have Not Been Patched to Address Critical Security Vulnerabilities

Citrix has recently disclosed two critical security vulnerabilities, designated as CVE-2022-27510 and CVE-2022-27518, that affect thousands of its Application Delivery Controller (ADC) and Gateway endpoints. These vulnerabilities have been assigned CVSS scores of 9.8 and pose significant risks to affected systems. The first vulnerability, CVE-2022-27510, allows for the bypass of authentication controls and the unauthorized access to Gateway user capabilities.
The second vulnerability, CVE-2022-27518, allows for the execution of remote code and the potential takeover of affected systems. Citrix released patches for these vulnerabilities on November 8 and December 13, 2022, respectively. It is important for users of Citrix ADC and Gateway systems to ensure that they have applied these patches to protect against these vulnerabilities.
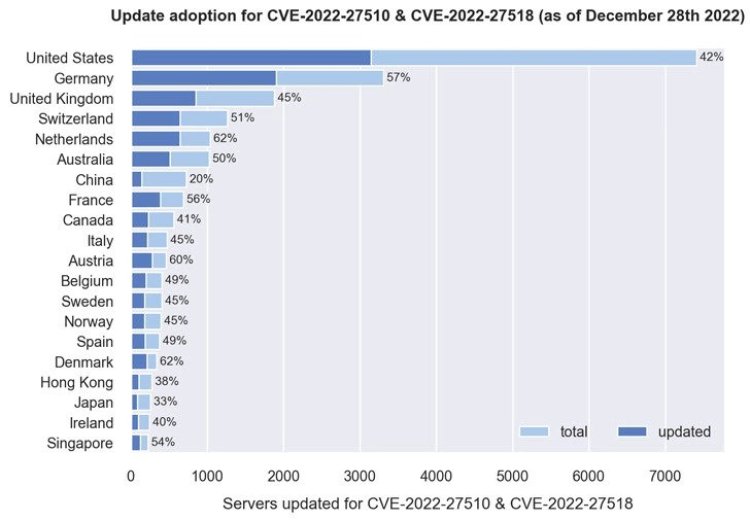
Earlier this month, Citrix and the U.S. National Security Agency (NSA) warned that the vulnerability designated as CVE-2022-27518 is being actively exploited by threat actors, including the APT5 group linked to China. According to a new analysis by the Fox-IT research team at NCC Group, thousands of internet-facing Citrix servers are still unpatched and therefore vulnerable to hacking.
This includes over 3,500 Citrix ADC and Gateway servers running version 12.1-65.21 that are susceptible to CVE-2022-27518, as well as more than 500 servers running 12.1-63.22 that are vulnerable to both vulnerabilities. Approximately 5,000 servers are running version 13.0-88.14, which is immune to both vulnerabilities.
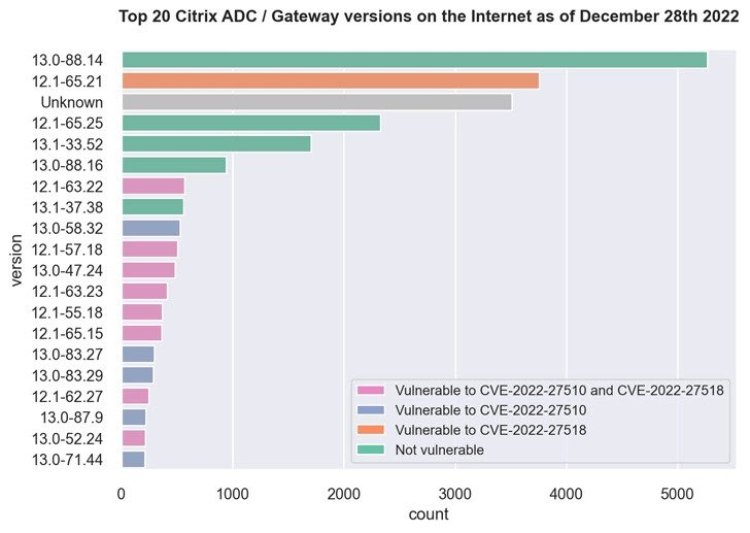
Fox-IT's analysis shows that a majority of the servers that have been patched are located in France, Austria, Denmark, the Netherlands, Germany, Singapore, Australia, the U.K., and the U.S., while China has the lowest patching rate, with only 20% of its nearly 550 servers having been updated. Fox-IT determined the version information by examining the MD5-like hash value present in the HTTP response of the login URL ("ns_gui/vpn/index.html") and mapping it to the corresponding versions.
Source: The Hacker News
 Alexander
Alexander